Hello I'm
Zahid Hasan
Cyber Security Expert
I'm a passionate cybersecurity professional with a knack for innovative solutions and hands-on experience in encryption, ethical hacking, and advanced threat detection. My commitment to securing digital landscapes is matched only by my drive to continuously learn and adapt in the ever-evolving field of cybersecurity.
Get started Learn more.png)

About me
Currently pursuing a Bachelor's in Computer Science, specializing in Cybersecurity, I have hands-on experience in ethical hacking, vulnerability assessment, and network security. My diverse skill set includes cryptography, AWS, Git, and AI, making me adept at tackling complex cybersecurity challenges.
- Certified Cybersecurity professional with Experience in Offensive security.
- Skilled in creating effective cybersecurity tools in Python.
- Published author specializing in AI-based stock market prediction.
Skills
I started my journey in cybersecurity with a deep curiosity and a desire to understand the intricate workings of technology's security landscape, leading me to pursue a Bachelor's degree in Computer Science with a specialization in Cybersecurity.
Ethical Hacking
Demonstrated ability to identify and exploit vulnerabilities in systems to improve security measures.
Network Security
Proficiency in implementing and managing secure networks to protect against unauthorized access and cyber threats.
Cryptography
Knowledge of cryptographic algorithms and protocols to secure data and communications.
Penetration Testing
Experience in simulating cyber attacks to evaluate the security of systems and networks.
AWS (Amazon Web Services)
Competence in using AWS services to build and deploy secure and scalable applications.
Shell Scripting
Proficient in writing scripts to automate tasks and manage systems, enhancing efficiency and security.
why choose me
I possess a robust blend of ethical hacking expertise, network security skills, and proficiency in cryptography and shell scripting, making me exceptionally equipped to tackle complex cybersecurity challenges.
Provide Advanced Security for Advanced Threat
Multiple layers of security are dispersed the computers, networks, programs, or data that one wants to keep secure.
-
Certified and Professional Expert
For business to have a successful defence against cyber attacks, the people, processes, and technology.
-
Security on a global scale
By automating interconnections across a few Cisco is a security products for the cyber security.
-
24/7 Premium Support
Unified threat management system may the speed is up crucial security operations tasks Like detection, investigation.

It takes 20 years to build a reputation and few minutes of cyber-incident to ruin it.
Hire me to ensure your website, web servers, and web apps are protected by complete and tested solution suites. Shield, the world leader in automotive cybersecurity, leverages advanced threat protection to safeguard your digital assets.
Get startedProjects
I'm Working On A Variety Of Technologies Right Now, Secure Shell (SSH), Cybersecurity, And Cryptography.

Encryption Decryption Tool
This project provides a simple graphical user interface (GUI) for encrypting and decrypting files and directories on your computer's drive.
Skills learned
- Cryptography
- Bash Shell Scripting
- PythonAesCrypt

Subdomain Enumeration Tool
The Subdomain Enumeration Tool efficiently discovers target domain subdomains using Python, optimized HTTP requests, and multiprocessing.
Skills learned
- Subdomain Enumeration
- HTTP Protocol
- Python Parallel Computing

Password Generator
A simple yet powerful password generator script written in Bash to generate secure passwords
Skills learned
- Base64 Encryption
- Shell scripting
- Command Line Interface(CLI)
NFT Web Security System
The opportunity to keep one step ahead of the next wave of the viruses, malware, and other online dangers.
Analyze The Current Security Posture
- Malware Detection Removal
- Remember To Log Off Shop
- Safety In Trusted Websites
SSH Exploitation Tool
The SSH Exploitation Tool is a Python script for brute-forcing SSH passwords using a wordlist.
Skills learned
- Proficiency in Python programming.
- Understanding of SSH manipulation.
- Knowledge of cybersecurity practices.
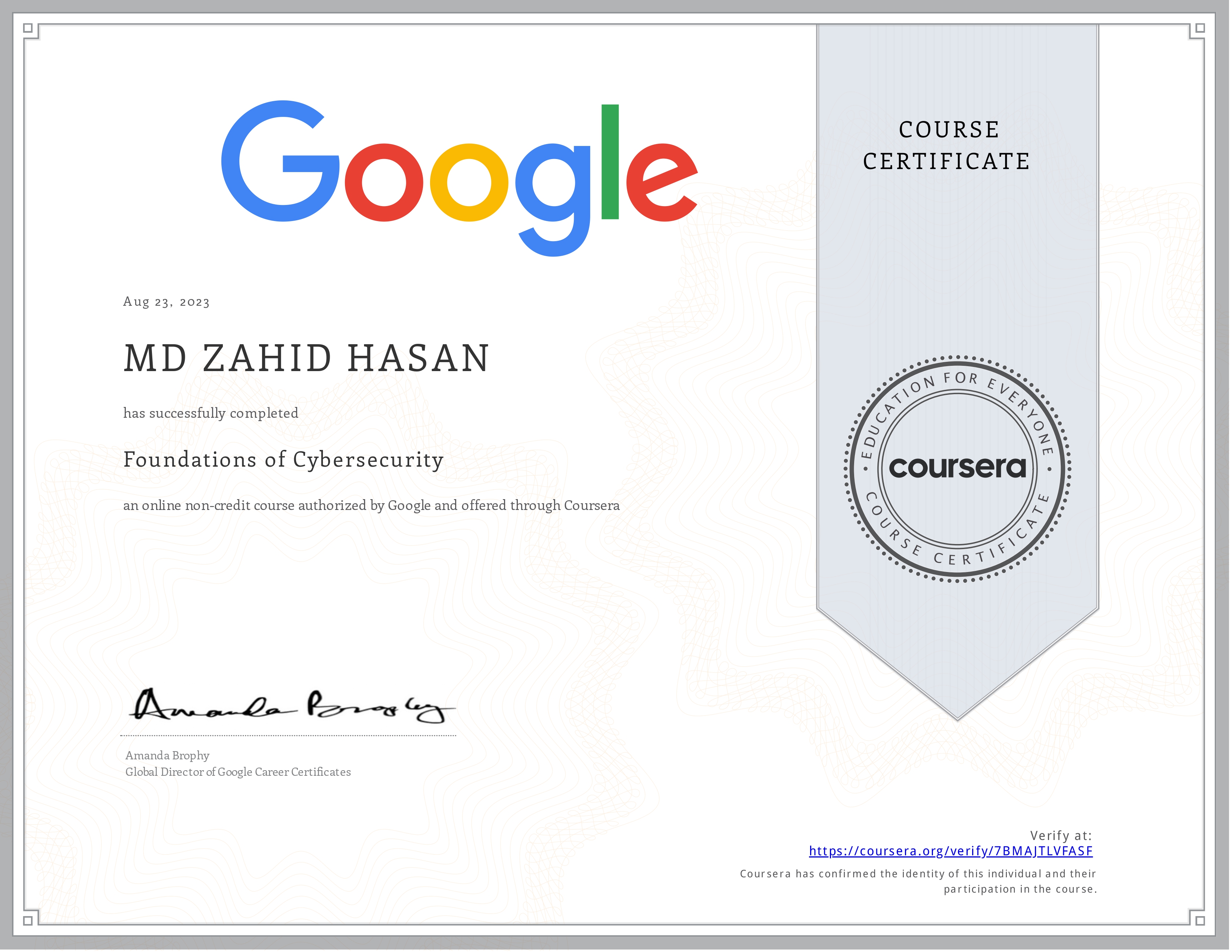
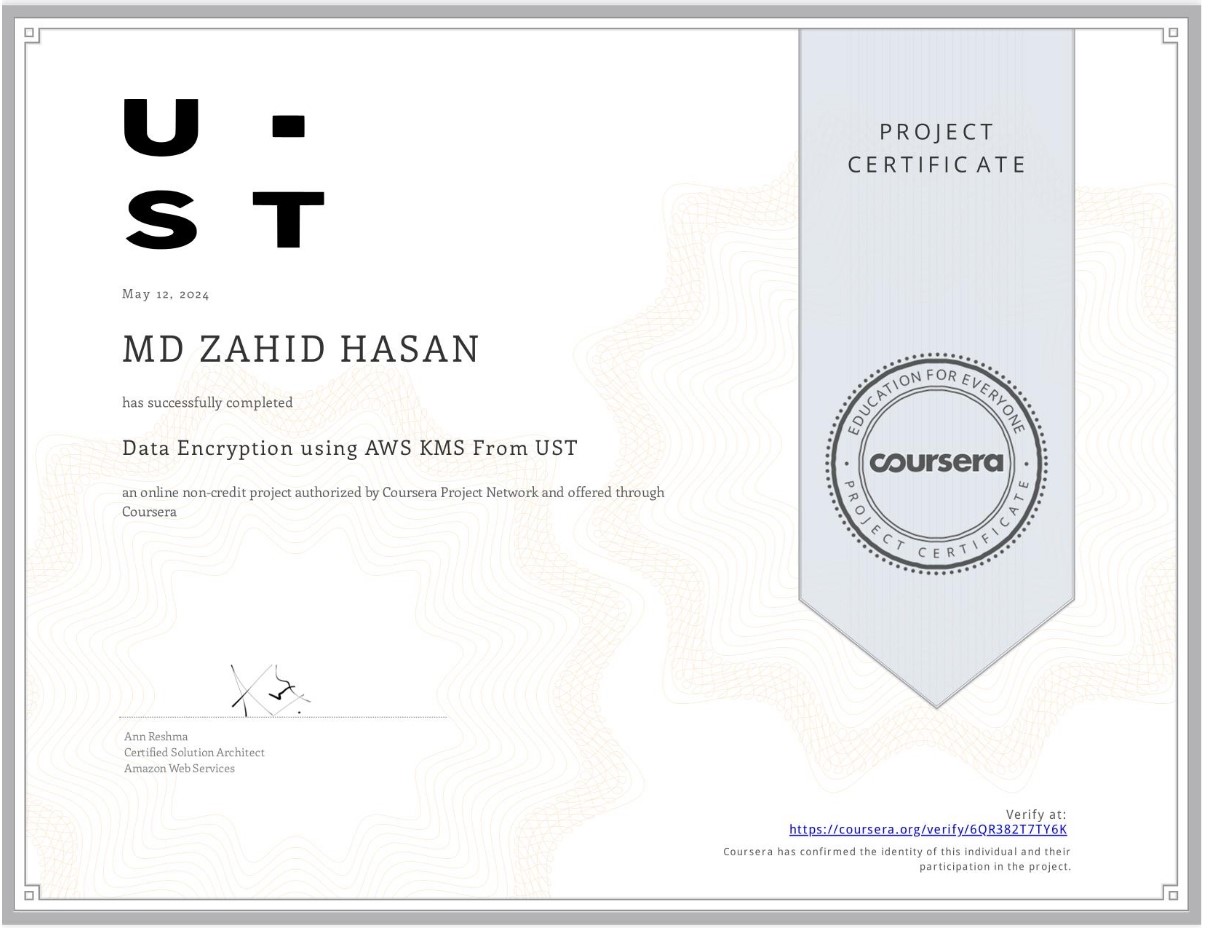
Certifications
Here are the certifications I hold in cybersecurity.
Get in touch with me
I'm an Cyber Security specialist with experience in a variety of related fields, including network security.
©2024 Zahid Hasan. All Right Reserved